In this article, we will explore how to manage Windows driver updates with Intune. Microsoft Intune can help you create, deploy, and manage Windows Driver update policies for your Windows 10 and Windows 11 devices.
Until now, most organizations had to rely on third-party tools to distribute driver updates for Windows devices in Intune. Microsoft has finally come up with a solution to deploy Windows driver updates and firmware updates using Intune with a proper procedure.
Windows driver update policies in Intune allow you to view the list of available driver updates that are applicable to the devices targeted by the policy, approve updates for deployment, or pause the deployment of individual updates. When driver updates are approved, Intune sends the assignments to Windows Update, which manages the update installation on devices based on the policy configuration.
Microsoft has launched policies and reports for managing Windows driver and firmware updates in Microsoft Intune. In two ways, this new Intune feature makes it easier to keep drivers on your Windows devices up-to-date. To begin, you will no longer be required to perform the manual tasks of downloading, repackaging, and deploying drivers using generic tools. Instead, you can use the Windows Update for Business deployment service’s driver update management settings and reports.
This step-by-step guide aims to assist you with all the required steps to manage driver updates with Intune for your organization. If you are planning to deploy firmware updates and driver updates with Intune, this enterprise deployment guide is for you.
Benefits of deploying Windows Driver updates using Intune
As per the announcement by Microsoft, these new capabilities are part of the Intune Windows Enterprise offerings. The following are the advantages of using Intune to deploy Windows driver updates:
- Intelligent servicing helps identify which driver updates are available for devices in the policy.
- Options to choose whether you want to deploy driver updates automatically or manually approve the updates and then target them to Windows devices.
- You can rely on trusted quality thanks to prior certification and validation by numerous device manufacturers.
- Intune offers more granular controls that allow you to pause the deployment of a particular driver. You can also resume the driver update deployment on demand.
- In addition to the recommended updates, optional drivers and firmware are available.
- Detailed reporting is built into Intune to help you monitor device status, alerts, and recommendations for remediation.
- Windows Autopatch automatically creates driver policies that allow you to roll out drivers and firmware across your deployment rings (unless you opt out of the service), with more granular controls coming later this year. Driver Updates aren’t supported during autopilot at this time.
See Also: Step-by-Step Windows Autopilot Setup Guide
Windows Driver Update Management Architecture
The below architecture diagram by Microsoft will help organizations that are planning to utilize Intune to manage Windows driver updates for their devices.

Here are some key points about the Windows driver update management architecture diagram shown above:
- Microsoft Intune (MDM) provides the Azure Active Directory IDs and Intune policy settings for devices to WUfB-DS. Intune also provides a list of driver approvals and pause commands to WUfB-DS.
- Based on the data provided by Intune, WUfB-DS configures Windows Updates. Windows Updates provides the applicable driver update inventory per device ID.
- Firmware updates published in WU do not require the BIOS/UEFI to be unlocked.
- Devices send data to Microsoft so that Windows Update can identify the applicable driver updates for a device during its regular Windows Update scans for updates. Any approved updates install on the device.
- WUfB-DS reports Windows diagnostic data back to Intune for reports.
Also Read: Download the Latest Microsoft Intune Architecture Diagram
Prerequisites for using Windows Driver Update Management with Intune
To use Windows Driver Update Management in Intune, you must first ensure that all prerequisites are met. To manage driver updates for your Windows devices efficiently, your organization must have the following licenses, subscriptions, and network configurations.
Subscriptions
The following subscriptions are mandatory for Windows driver update management with Intune.
- Intune: Your tenant requires the Microsoft Intune Plan 1 subscription.
- Azure Active Directory (Azure AD): Azure AD Free (or greater) subscription.
Windows Device and Edition Requirements
The device and edition requirements ensure that your devices are capable of managing Windows Driver Updates in Intune. Your organization must have one of the following subscriptions that include a license for the Windows Update for Business deployment service:
Subscriptions for Devices
- Windows 10/11 Enterprise E3 or E5 (included in Microsoft 365 F3, E3, or E5)
- Windows 10/11 Education A3 or A5 (included in Microsoft 365 A3 or A5)
- Windows Virtual Desktop Access E3 or E5
- Microsoft 365 Business Premium
Windows Editions
Coming to Windows Editions, the Driver updates are supported for the following Windows 10/11 editions:
- Pro
- Enterprise
- Education
- Pro for Workstations
Windows Device Requirements
In addition to the prerequisites listed above, the following Windows device requirements are critical.
- Windows driver update management in Intune applies to Windows 10 and Windows 11. You must be running a version of Windows 10 or 11 that remains supported.
- The Windows devices should be enrolled in Intune MDM and be Hybrid AD joined or Azure AD joined. Learn how to enroll Windows 11 devices in Intune.
- Have Telemetry turned on, with a minimum setting of Required. You can configure Telemetry as part of a Device Restriction policy for Windows 10/11. In the device restriction profile, under Reporting and Telemetry, configure share usage data to use a minimum value of Required.
- The Microsoft Account Sign-In Assistant (wlidsvc) service should be able to run on Windows devices. This service enables user sign-in through Microsoft account identity services. If the service is blocked or set to Disabled, it fails to receive the update. By default, the service is set to Manual (Trigger Start), which allows it to run when needed.
- The Windows endpoints should have access to the network endpoints required by Intune. To manage devices behind firewalls and proxy servers, you must enable communication for Intune.
RBAC requirements
To manage Windows Driver updates with Intune, your account must be assigned an Intune role-based access control (RBAC) role that includes the following permissions:
Device configurations
- Assign
- Create
- Delete
- View Reports
- Update
- Read
Enable Windows Data Collection for Reports in Intune
Some Intune features, including Windows update reports, require sharing Windows diagnostic data with Intune. You must enable the use of Windows diagnostic data in Intune to support reporting for Windows Driver updates. Diagnostic data may already be enabled for other reports, such as Windows Feature updates and Accelerated Quality Update reports.
Use the following steps to enable the use of Windows diagnostic data:
- Sign in to the Microsoft Intune admin center and go to Tenant Administration > Connectors and Tokens > Windows Data.
- Expand Windows data and ensure the setting Enable features that require Windows diagnostic data in processor configuration is toggled to On.

Prepare a Driver Deployment Plan in Intune
Microsoft advises creating a plan for deploying driver updates that includes team members who can certify both driver and firmware changes. It’s beneficial to have a committed group of Intune admins who are knowledgeable with Windows drivers and concepts that are connected to them. These are only the recommendations that Microsoft suggests while preparing a deployment plans for Windows drivers.
- Decide the approval method for Windows drivers: You must choose between Automatic approval and Manual approval methods, depending on how you want the drivers to be approved and deployed.
- Use deployment rings for driver update policies: Enterprise administrators can limit the installation of new driver updates to test groups of devices before broadly installing those updates on all devices by using the deployment rings for driver update policies. By using this strategy, your team can spot potential problems before updates are widely distributed. Utilizing rings can give you enough time to postpone or stop the deployment of a problematic update in later rings.
- Configure the driver availability for Windows Devices: This is a practical option if you want to reduce the number of restarts on end machines when you deploy drivers with Intune. You can set the update availability for manually approved updates to match common update cycles like Microsoft’s Patch Tuesday release. Alignment of schedules can help reduce the extra system restarts that some driver updates require.
- Prevent Driver Update Policy Conflicts: Intune administrators managing driver updates must assign devices to only one driver update policy to help prevent a device from having its drivers managed through more than one policy. This can help avoid having a driver installed in one policy when you previously declined or paused that same update in a separate policy.
- Rollback Driver Updates With Intune: Deploying driver updates for Windows devices is easy with Intune, but rolling back an update is difficult. WUfB doesn’t currently support Driver rollback, and therefore you must carefully approve the driver updates. If you must remove a driver update from remote Windows devices, consider manual methods like PowerShell scripts.
Useful Article: How to Configure Multiple Admin Approvals In Intune
Windows Driver Updates Approval Methods: Automatic vs. Manual
When you create Windows Driver Update Policies in Intune, at some point you’ll need to specify the approval method for driver updates. For policy approval and deployment settings, there are two options to choose from: Automatic and Manual. Let’s understand what each option means.
- Manually approve and deploy driver updates: With this option, each new driver update added to the policy has its status set to Needs review. Each update’s status must be changed to Approved in the policy before it can be pushed to supported devices. When you manually approve an update, you can specify a date on which it becomes available for Windows Update to install on applicable devices. This date is distinct from the deferral period that is required for automatically approved updates in policies that use automatic approvals.
- Automatically approve all recommended driver updates: With this option, all new recommended driver updates that are added to the policy are added with a status of “Approved“. Once the updates are set to approved, they begin to install on applicable devices without having to be reviewed or approved by an admin. Use an automatic approval policy when you want to ensure the drivers on your devices remain current with the OEM’s latest recommended update.
Note: If you are deploying Windows driver updates for the first time to your Windows devices managed by Intune, we recommend going with the Manual approval method. By selecting this method, you get to approve the drivers released by OEM and deploy only the ones that you require.
Manage Windows driver updates with Intune: High-Level Steps
Microsoft recommends a methodical approach to creating and managing driver update policies in Intune. Following are the high-level procedures Microsoft recommends for managing Windows driver and firmware upgrades with Intune.
- Create a driver update profile and deployment rings in Intune.
- Review the available drivers.
- Manually approve the Windows Drivers.
- Pause Windows Drivers.
- Monitor the drivers and Firmware Updates with built-in Reports.
Step 1: Create Windows Driver Update Policies in Intune
Use the following procedure to create a policy to manage Windows driver updates in Intune:
- Sign in to the Microsoft Intune admin center.
- Go to Devices > Windows > Driver updates for Windows 10 and later.
- Select Create Profile to create a driver update policy.

On the Basics tab of the driver update profile, specify the name and description. In the screenshot below, the following details are specified.
- Name: Windows Driver Update Policy
- Description: Manage Windows Driver Updates with Intune for Windows 10 and Windows 11 devices.
Click Next.

On the Settings tab, configure the approval method for driver updates in this policy. We have discussed the differences between the automatic drivers approval and manual approval methods in the earlier section. However, for your understanding, there are two options, and you must select one of the following options for the approval method:
- Manually approve and deploy driver updates: Before an update can be deployed to applicable devices, an administrator must edit the policy and change the status of each individual update to Approved
- Automatically approve all recommended driver updates: With this option, all new recommended driver updates that are added to the policy are added with a status of “Approved” and begin to install on applicable devices without having to be reviewed or approved by an admin.
For the current driver update policy, we have selected the option “Manually approve and deploy driver updates“.

Automatic Driver Updates Approval Method options
When you set a policy for automatic approvals, you must configure the following setting that creates a deferral period for the automatically approved updates:
Make updates available after (days): This setting is a deferral period that delays when Windows Update begins to deploy and install the new recommended update that was automatically added to the policy with a status of Approved. The delay supports from 0 to 30 days and starts from the day the update is added to the policy, not from the date the update was made available or published by the OEM. The deferral is intended to provide you with time to identify and, if necessary, pause deployment of the new recommended update.

For example, consider a driver update policy that uses automatic approvals and has a deferral of three days. On June 1, WUfB-DS identifies a new recommended driver update that applies to devices with this policy and adds the update to the policy as approved. Due to the deferral period of three days, Windows Update waits to offer this update to any device until June 4, three days after it was added to the policy. If the deferral was set to zero days, Windows Update would begin installing the update on devices immediately.
Select the Scope tags for the driver update profile. This is an optional step and if you would rather not assign scope tags, click Next.

On the Assignments tab, click on Add groups and select the Azure AD groups to which you want to assign the driver updates policy. Click Next.

For Review + create, review the policy configuration, and then select Create. When you select Create, your changes are saved, and the profile is assigned. Shortly, you’ll receive two separate notifications upon the creation of Windows driver updates policy.
- Windows driver update deployment successfully created
- Windows driver update deployment successfully assigned

Select your policy approval and deployment settings. Choose to set up a policy to approve and deploy updates automatically or manually. The approval method cannot be changed once a policy is created, but changes to individual driver approvals and deployment details will be possible once an inventory is built for assigned devices.
Step 2: Review Available Windows Driver Updates in Intune
Once you’ve created the policy, let devices scan for updates for about a day or so. On the Windows Driver update policy page, you get the “Sync” option to manually initiate the sync for latest drivers. This option basically checks for the latest drivers released by OEM’s for your devices. When you initiate the drivers sync, you’ll see the status as Last Sync: Pending initial inventory collection. It may take up to 24 hours for the driver update inventory to be returned.
Note: Intune to WUfB-DS syncs run each day, and you can use the Sync option to run a synchronization on demand. The time to complete a synchronization depends on the device information involved, but should usually take only a few minutes to complete.
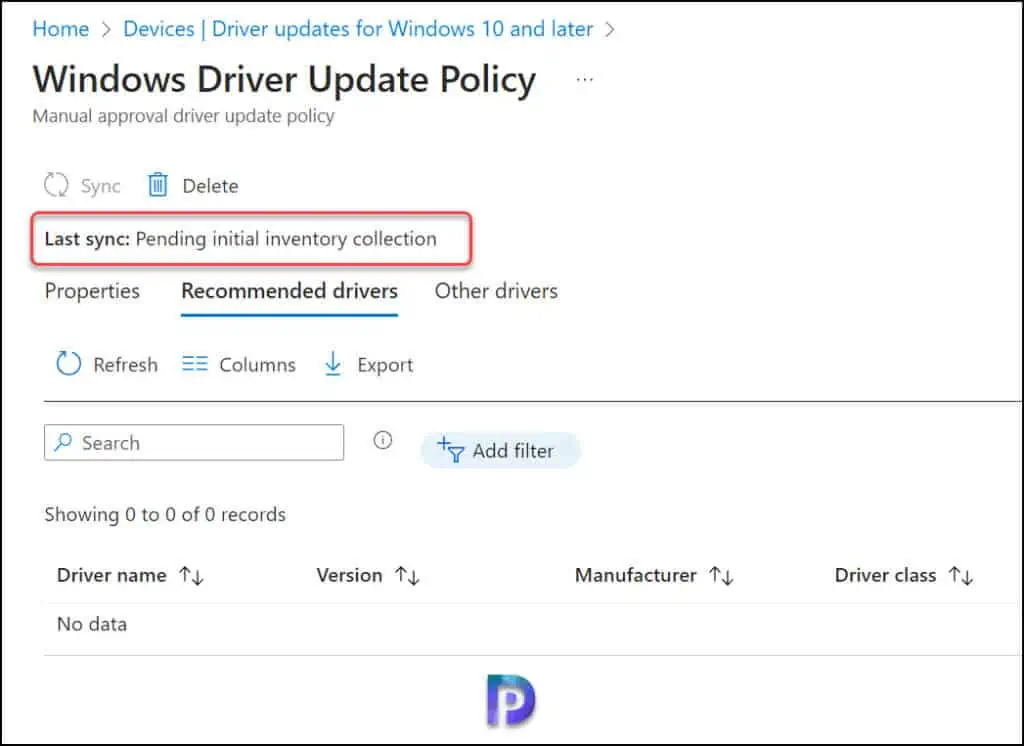
Once the driver updates synchronization is complete, the ‘Drivers to review‘ column will include the count of new recommended driver updates ready to review for manual approval. In an automatic policy, Drivers to review will stay at 0 since recommended drivers are automatically approved. This is a great indicator that new drivers have been discovered and are awaiting a decision whether to approve or decline deploying those drivers.
In the screenshot below, we see there are 3 driver updates which are marked for review.

To view the drivers that are populated in Intune, select the driver details under the Drivers to review column. The Recommended Drivers and Other Drivers tab displays all the Windows driver updates that are populated by your policy. Each of these drivers have their status set to Needs review. This is because you have set the Windows driver approval method to Manual, and hence they must be approved by admins manually.

Step 3: Approve Windows Drivers in Intune
When you open the policy, you can see both “Recommended Drivers” and “Other Drivers“. To approve a driver, follow these steps:
- Select the driver from the Driver name column.
- Select the Approve option under Actions in the flyout to Manage driver.
- Specify the date to make the driver available to devices when they scan Windows Update.
- The drivers are now marked as ‘Approved‘ as shown in the Status column.

Every driver that you manually approve will change it status from ‘Needs Review‘ to ‘Approved.’

Step 4: Optionally pause driver updates
After you manually approve the driver updates in Intune, you can ‘Pause‘ them to prevent any devices that haven’t yet received the update from being offered that update. When you pause an update, WUfB-DS removes the approval. If you have mistakenly approved a driver update or determined that the driver that you approved isn’t required, you can pause it. Needless to say, to pause an update, the update must have been approved.
You can pause driver updates in Intune with following steps
- Go to the Driver Update Policy and select the driver from the Driver name column.
- On the Manage Driver flyout, under the Actions, click the drop-down and select Pause.

The status of the driver update is now changed from Approved to Paused.
Note: If a device hasn’t yet scanned for the update when you pause Windows driver updates, the paused update isn’t offered, and Pause functions as intended. When a device checks for updates and finds that a driver update has been paused and is currently downloading, installing, or waiting to restart, Windows Update makes a “best effort” to prevent the driver update from being installed.

Conclusion
We hope this article helped you to manage Windows driver updates with Intune, and all the screenshots were helpful. With driver update policy in Intune, you can review, approve for deployment and pause deployments of driver updates for your managed Windows 10 and Windows 11 devices. The driver updates in Windows Autopilot are not currently supported. However, the good news is Microsoft is working on including the ability to deploy optional drivers, maintain manual control over driver approvals at the ring level, and to use these functions for your custom Autopatch groups.













Is it possible to Approve mutliple optional Driver Updates or do we need to approve every single update by clicking and choosing the approve Button.
Some kind of Powershell Script?
If Intune does an BIOS update, will it trigger the bitlocker on the workstation and the need for the key?
It worked for us with Lenovo Clients without needing the Bitlocker Key. Don’t know how it is with other manufacturer.
We have several models from different vendors in our environment. Is it recommended to create an Azure AD Group for each model and create a Drive Updates Profile for each model? What are the best practices I guess when you have several models in your environment?
When enabled, what happens if someone connects a new local printer to their machine? Will it still serach and find a suitable print driver or will it first need to appear in the list and required to be approved before the print driver are installed?
In the past, simply setting “Windows drivers – Allow” in the Update Ring has been enough to receive driver & BIOS updates. Do we now NEED the new policy to continue receiving drivers?
The new policy offers more control over the drivers deployment.
Does this mean that patching workload for co-managed devices must be moved to Intune, so we can’t use Driver patching option only from Intune and security patches from Config Manager?