Disable User Account Control Using Group Policy User Account Control feature basically aims to improve the security of Microsoft Windows by limiting application software to standard user privileges until an administrator authorizes an increase or elevation. In this way, only applications trusted by the user may receive administrative privileges, and malware should be kept from compromising the operating system. In other words, a user account may have administrator privileges assigned to it, but applications that the user runs do not inherit those privileges unless they are approved beforehand or the user explicitly authorizes it. If you have administrator privileges on your PC, you can also fine-tune UAC’s notification settings in Control Panel.
When changes are going to be made to your computer that require administrator-level permission, UAC notifies you. If you are an administrator, you can click Yes to continue. If you are not an administrator, someone with an administrator account on the computer will have to enter their password for you to continue. If you give permission, you are temporarily given the rights of an administrator to complete the task and then your permissions are returned back to that of a standard user. This makes it so that even if you’re using an administrator account, changes cannot be made to your computer without you knowing about it, which can help prevent malicious software (malware) and spyware from being installed on or making changes to your computer.
Disable User Account Control Using Group Policy
We will create a group policy and define the settings to disable the UAC.
First open the Server Manager Console and click on Tools. Now click Group Policy Management from the drop down. Right click on the domain and click on Create a GPO in this domain and link it here. Provide a suitable name to the GPO and right click the policy and click on Edit.
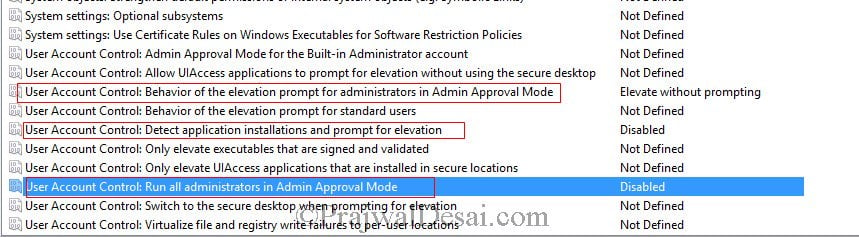
In the GPMC editor click on Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options. On the right pane there are lot of settings that you see, so you need to modify the following policies.
1) User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode = Right click policy setting, click Properties. Check the box Define this policy setting and choose Elevate without prompting.
2) User Account Control: Detect application installations and prompt for elevation = Right click policy setting, click Properties. Check the box Define this policy setting and choose Disabled.
3) User Account Control: Run all administrators in Admin Approval Mode = Right click policy setting, click Properties. Check the box Define this policy setting and choose Disabled.
Run gpupdate /force on Windows client machine. The logged on users might see a notification that a restart is required to turn off user account control. After the restart of the client machine you will see that UAC is set to Never notify on the client machine.















Thanks this helped allot
Hi All,
Is there a way to prevent users from updating/changing the settings.
We have already set the UAC settings to Always Notify. However users with admin access are changing it to never notify.
I was wondering if we have any option to block users from being turning it off.
is this works on Windows 11?
Hello Hi, I’m facing some issue in WDS&MDT Image Windows 10. Bcoz of UAC some applications are not installing through MDT(Few applications are installing without any error). Error is Application xxxx returned an unexpected return code: 1639
Schoolboy error – policy applied to wrong tree! working fine.
What I can say, is that ALL other policies are being applied correctly on the test machine
Hi, I have applied the settings above, and the policy is active on my test client machine – no reboot prompt requested, but Gpupdate /force applied and rebooted anyway. The policy failed to run. I am on Server 2012 r2 and windows 7 pro on the client. any ideas?
has the policy been applied to the computers ?. Did you check the rsop on client computers ?.
HI, I tried but I get an error when checking the test machine “RPC server is unavailable” which is odd because RPC is running on the machine
Unfortunately, the consequence of this action in Windows to is the inability run any system app such as Edge, Calc.exe, etc. Microsoft has for some reason, deemed it necessary to kill the administrator if UAC is disabled. While the fix above may deal with one issue, it creates an entire other set which are frankly, unacceptable. I guess I will have to find other apps other than native apps to run for my users. Microsoft is so incredibly inept, it defies words. UAC was never a solution. It was a dodge for Microsoft and a complete rouse. They just passed the buck to the user instead of fixing the security holes in their OS and apps. Chicken-hearted, feeble and irresponsible and even deplorable are some of the words which come to mind.
Is it possible to disable UAC in Windows Xp client when used in Windows server 2012 environment.
Windows XP ?.
I don’t think XP ever had UAC, it was introduced in Vista
i have joined this community also but not much more aware about this.
here you go – https://www.vmware.com/support/pubs/vsphere-esxi-vcenter-server-pubs.html
Sir,
i have created two machines under the VMWARE workstation and both are based out in a different domain and need to be communicated with each other, is there any possible ways to perform this ?
Have you created 2 domains in your lab setup ?. Or is it 2 machines ?.
i have created two diffrent domain.
yes i have created 2 domains.
hi i am new to vmware, guide where to start.
I would say here – http://www.vmware.com/in
i am in but what i have to do after this, please let me know.
@Sushant – Vmware has got lot of products, which one are looking specifically ?.
Boss, Vsphere