In this post we will see the steps for installing WSUS for SCCM, configuring firewall exceptions, opening ports for SQL replication.
So far in this deployment series of SCCM 2012 SP1, in the first post we saw the steps to install and configure active directory domain services.
In the second post we saw the steps to install SCCM 2012 SP1 prerequisites and in the third post we saw the steps to install SQL server for SCCM 2012 SP1.
WSUS is Microsoft’s separate, stand-alone server-based product for distributing updates to Windows systems. It also uses the WUA to scan for patch applicability and subsequently install updates delivered by WSUS.
WSUS 3.0 Service Pack 2 is required for System Center 2012 Configuration Manager. SCCM 2012 SP1 supports only 64-bit site systems, you must use the 64-bit version of WSUS on one of the supported 64-bit editions of Windows Server.
You can install WSUS by opening up the server manager, roles and by adding WSUS role. I prefer to install the WSUS by downloading the setup file from Microsoft.
We will be installing WSUS role on SCCM.PRAJWAL.LOCAL machine with the user account sccmadmin.
Installing WSUS 3.0 SP2 for SCCM
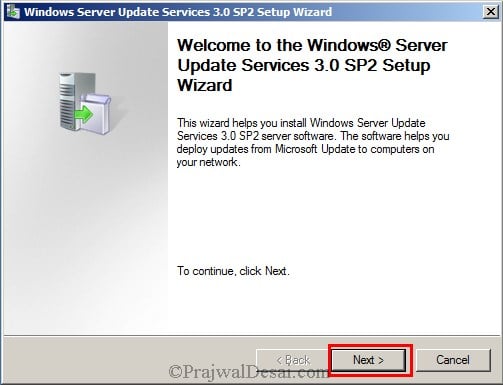
Using the below steps, you can install WSUS for SCCM. Double click the setup file to begin the installation. On the welcome page click on Next.
On the Installation Mode Selection, Choose Full server installation including Administrator Console. Hit Next.
Accept the license agreement and click on Next.
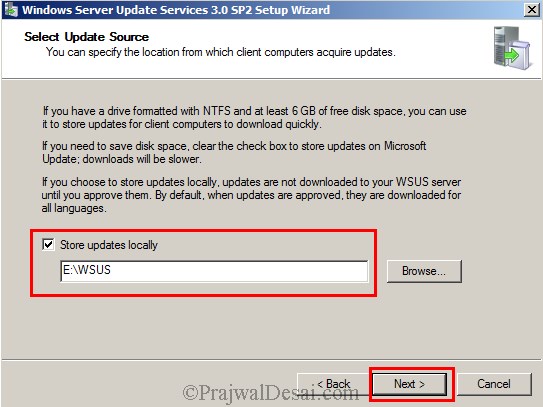
It is recommended to store the updates on a different drive instead of storing it on C: drive. In our example we will be storing the updates locally on E:WSUS path. Click on Next.
For Database Options we will not be using the internal database, instead we will use the SQL database instance. Choose Use an existing database server on this computer and click on Next.
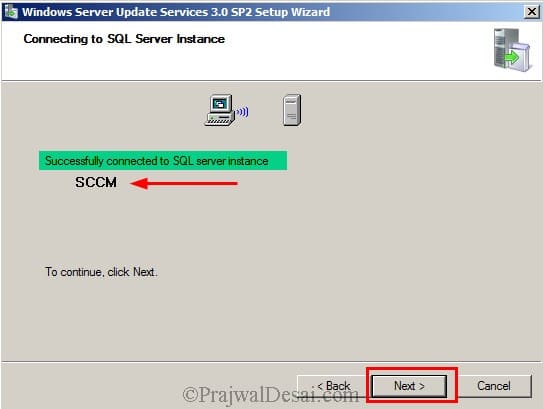
The SQL server is installed on the same server so it gets connected to SQL server instance quickly. If you have a SQL server running on other server select Using a existing database server on remote machine. You will have to provide the machine nameinstance to connect.
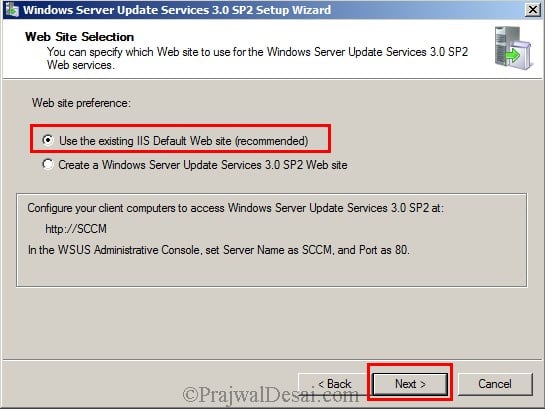
If you are planning to create a dedicated IIS site, then choose Create a Windows Server Update Services 3.0 SP2 Web Site, the port numbers for a dedicated site are 8530 and 8531 for Secure Socket Layer (SSL) connections. If you are planning to use a IIS default Website then Select “Use the existing IIS Default Web site” and click on Next.
Click Next.
We have successfully completed the WSUS installation for SCCM. Click on Finish.
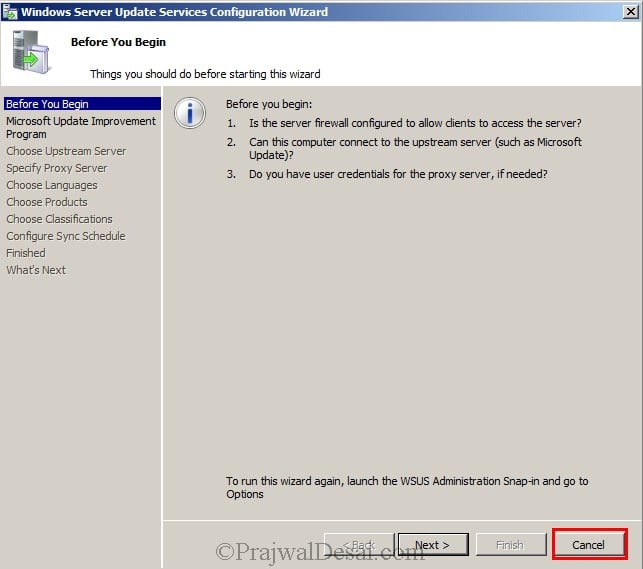
Once you click complete installing WSUS 3.0 SP2, the WSUS configuration wizard comes up. Do not configure it as we will be using SCCM to deploy the updates. This is an important step because most of you would configure this.Click Cancel to close the wizard.
After cancelling the WSUS configuration wizard, as a prerequisite you must install 2 updates for WSUS 3.0 SP2. Downloads are available for 32 bit and 64 bit systems.
Update for Windows Server Update Services 3.0 SP2 (KB2720211)
Update for Windows Server Update Services 3.0 SP2 (KB2734608)
Configuring Firewall for SCCM
To know what are the ports used in Configuration Manager 2012 SP1 , please go through this link :- http://technet.microsoft.com/en-us/library/hh427328.aspx. In order to successfully use client push to install the Configuration Manager 2012 SP1 client, you must add the following as exceptions to the Windows Firewall.
- Printer Sharing
- Windows Management Instrumentation (WMI)
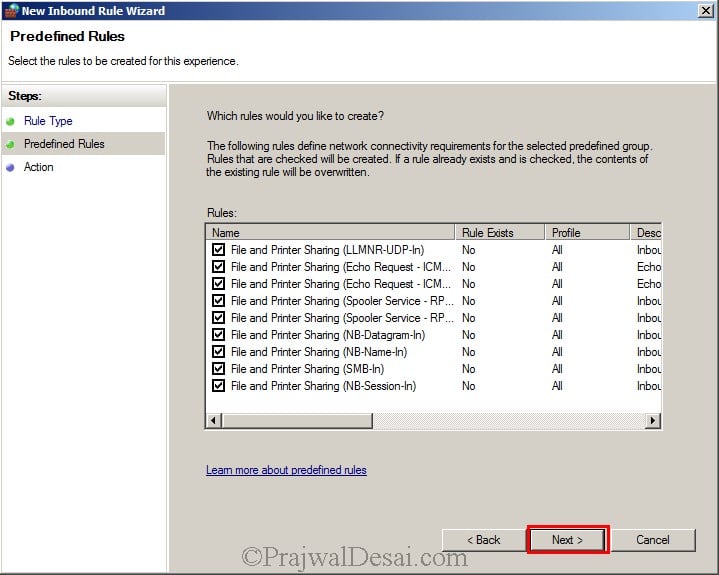
We will create an inbound and outbound rule, add File and Printer sharing service as exception to firewall and an Inbound rule to allow WMI. We will perform this activity on the Domain Controller.
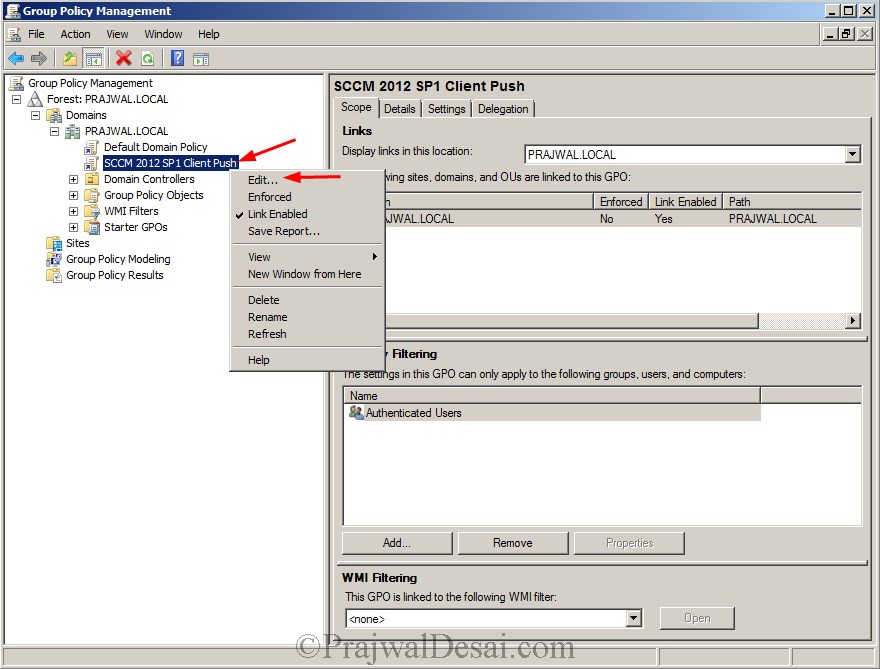
Click on All Programs, Administrative Tools, open Group policy management console. Right Click on the domain and Create a GPO. Provide a name to the GPO and click on OK.
Right click on the policy that you created and click on Edit.
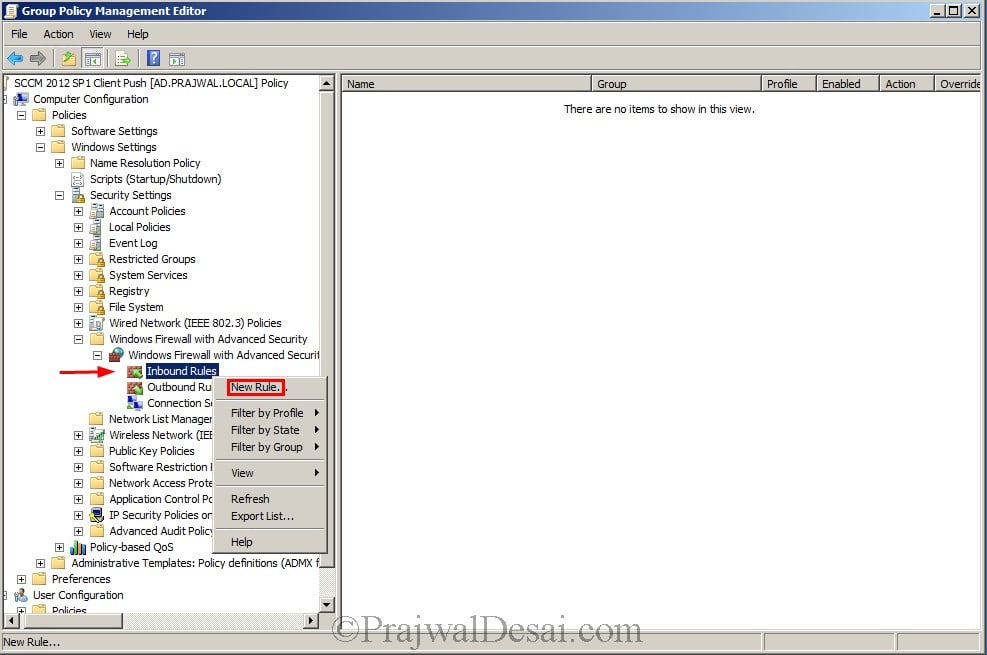
Expand computer configuration, Windows settings, Security settings, Windows firewall with advanced security. Right click on Inbound rules and click on New Rule..
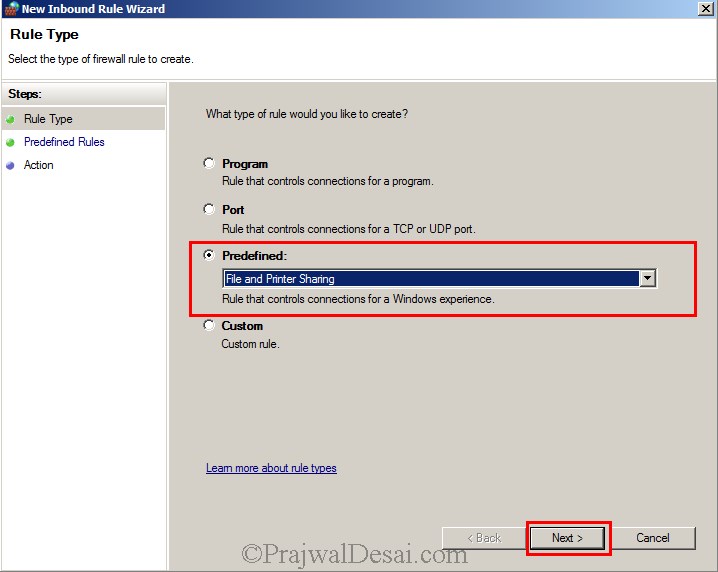
Click on Predefined and select File and Printer Sharing. Click on Next.
Click on Next.
Click on Allow the connection. Click Finish.
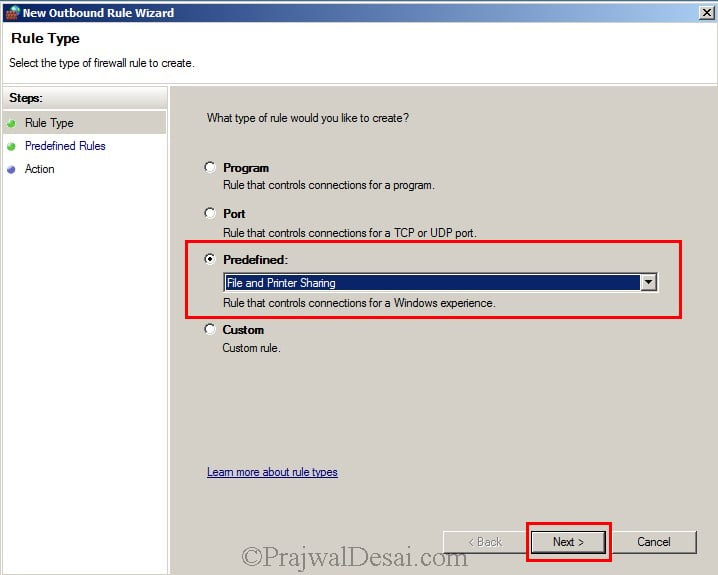
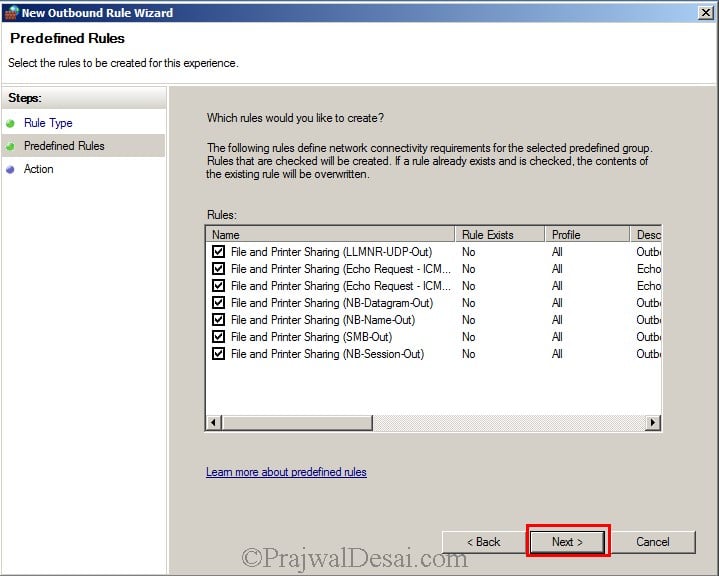
We have created an inbound rule to allow file and printer sharing, similarly right click on the Outbound Rule and click on New Rule. select File and Printer Sharing. Click on Next.
Click on Next.
Click on Allow the connection and click on Finish.
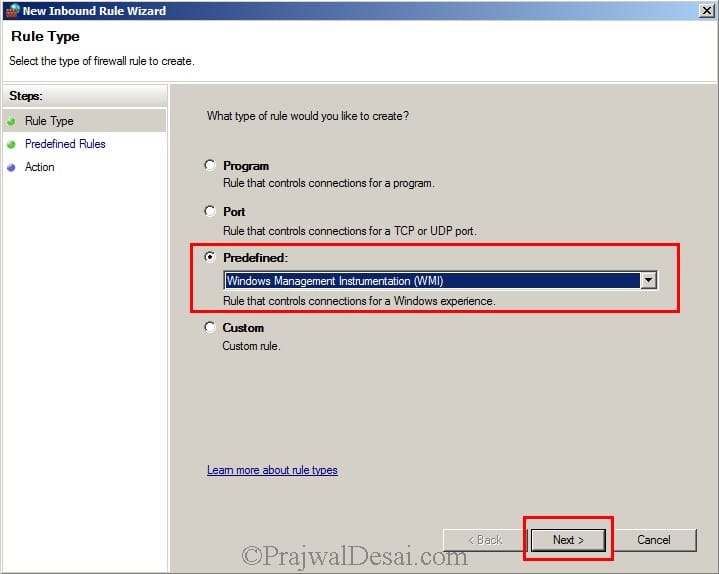
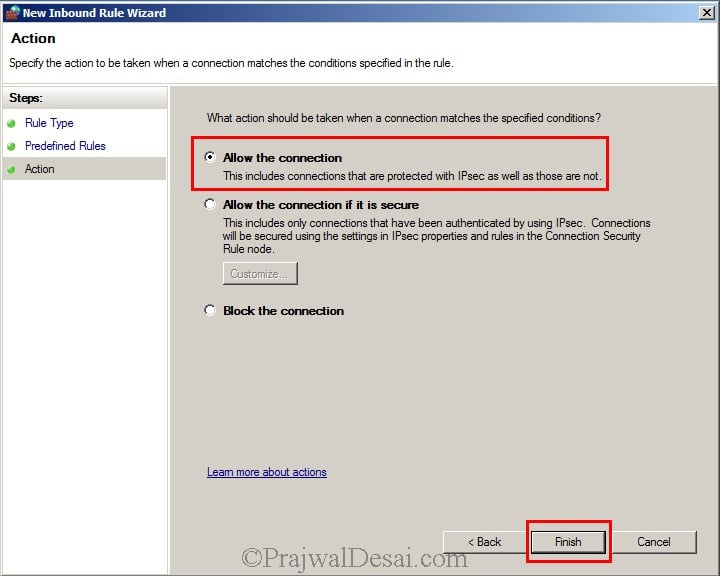
We need to create an Inbound Rule to allow the WMI service on our Firewall. So right click on Inbound Rule and click on New Rule. Click on Predefined and select Windows Management Instrumentation (WMI). Click on Next.
Click on Next.
Click on Allow the connection. Click on Finish.
Opening Ports for SQL Replication
Why should you open port 1433 and 4022 ??
Port 1433 – SQL Server listens for incoming connections on a particular port. The default port for SQL Server is 1433. It applies to routine connections to the default installation of the Database Engine, or a named instance that is the only instance running on the computer.
Port 4022 – This is SQL Service Broker, Though there is no default port for SQL Server Service Broker, but this is the port that we allow inbound on our firewall.
Script to Open the ports for SQL Replication
If you are looking for a script to open the ports for SQL replication here it is. Copy this script in the notepad and save it as opensqlports.bat. Right click on the batch file and run as administrator.
@echo off
echo ========= SQL Server Ports for SCCM ===================
echo.
echo.
echo **Right click on the batch file and Run As Administrator**
echo.
echo.
echo Adding SQL Firewall Exceptions for SCCM
echo.
echo Adding TCP 1433
netsh advfirewall firewall add rule name = "SCCM SQL (TCP 1433)" dir = in protocol = tcp action = allow localport = 1433 remoteip = localsubnet profile = DOMAIN
echo.
echo Adding TCP 4022
netsh advfirewall firewall add rule name = "SCCM SQL (TCP 4022)" dir = in protocol = tcp action = allow localport = 4022 remoteip = localsubnet profile = DOMAIN
echo.
echo Done adding firewall exceptions
echo..By default, Microsoft Windows enables the Windows Firewall, which closes port 1433 to prevent Internet computers from connecting to a default instance of SQL Server on your computer.
Connections to the default instance using TCP/IP are not possible unless you reopen port 1433. Therefore we will now create a group policy to open TCP ports 1433 and 4022.
Create a GPO to open TCP ports 1433 and 4022.
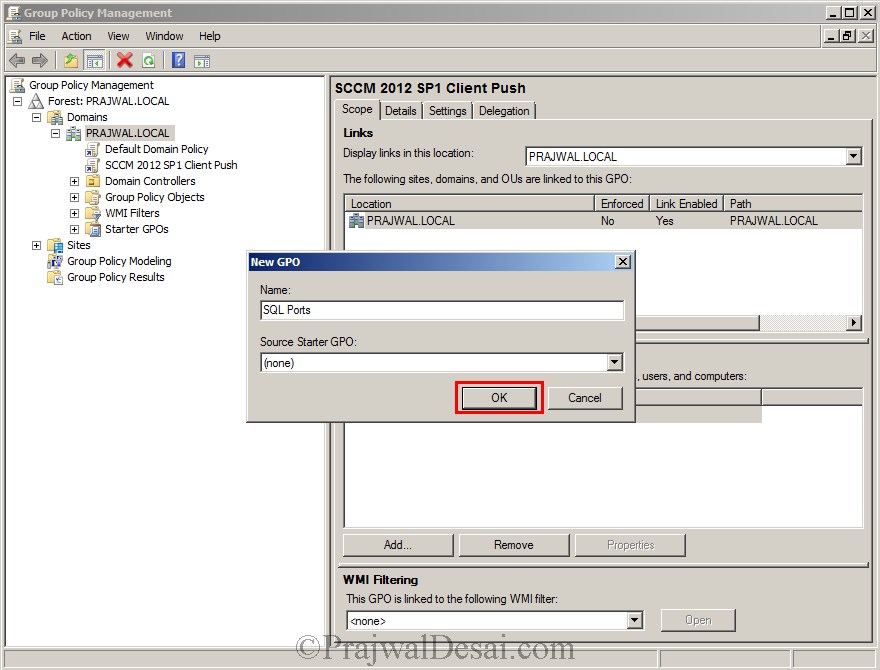
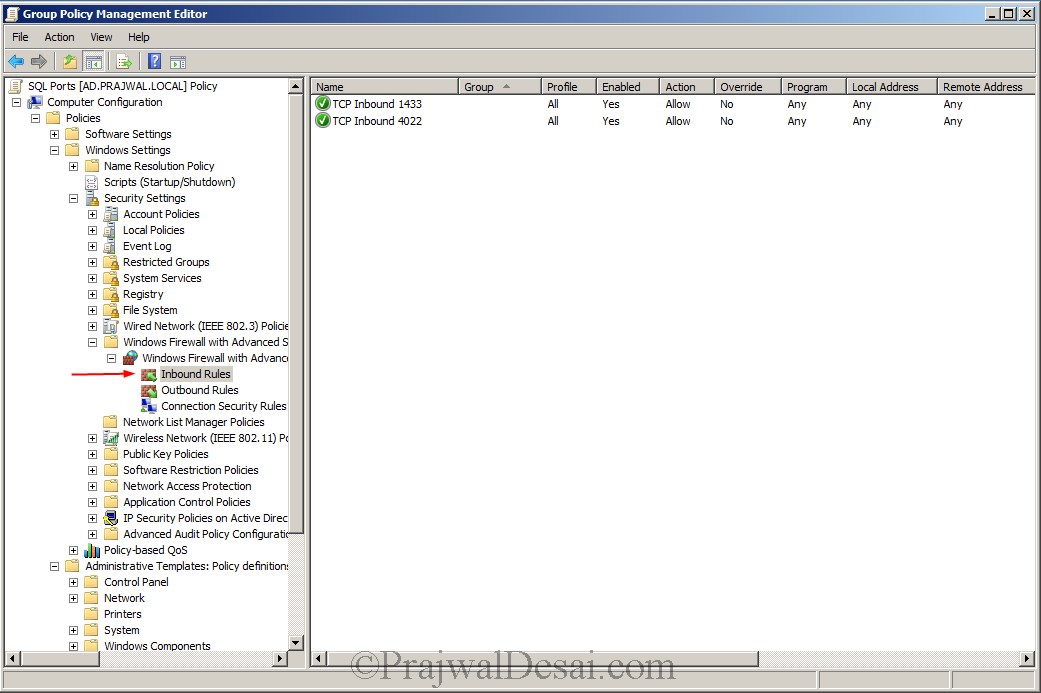
In case you choose to create a rule manually in firewall then open the Group Policy Management console. Create a new policy and name it as SQL Ports. Right Click the policy SQL Ports and edit it. In the Windows GP management console, expand computer configuration, Windows settings, Security settings, Windows firewall with advanced security.
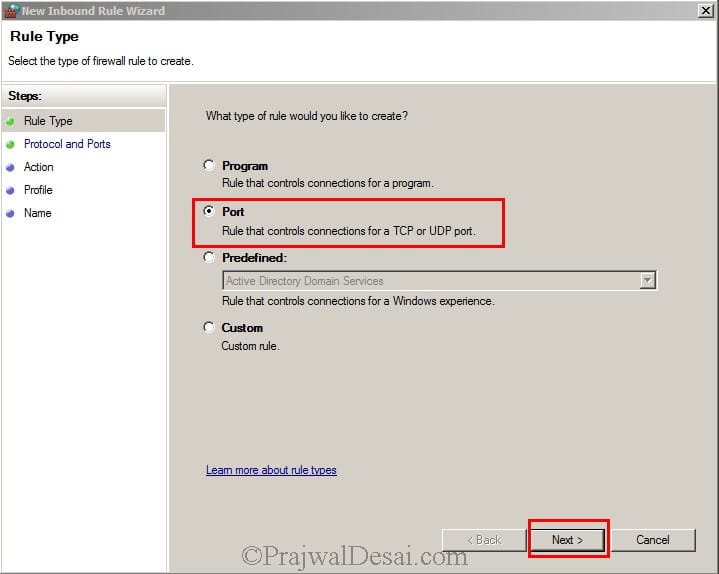
Right click on Inbound Rule and create an Inbound Rule and select Port. Hit Next.
Select TCP, and specify port 1433 in specific local ports.
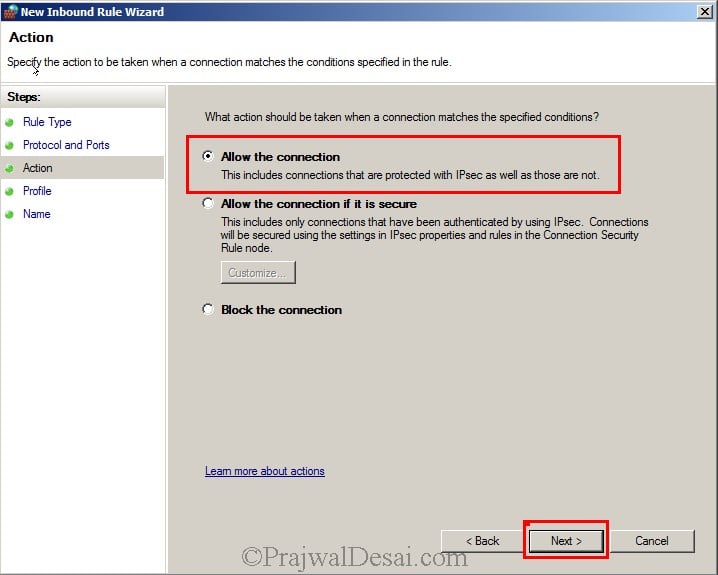
On the Action page, click Allow connection and hit Next.
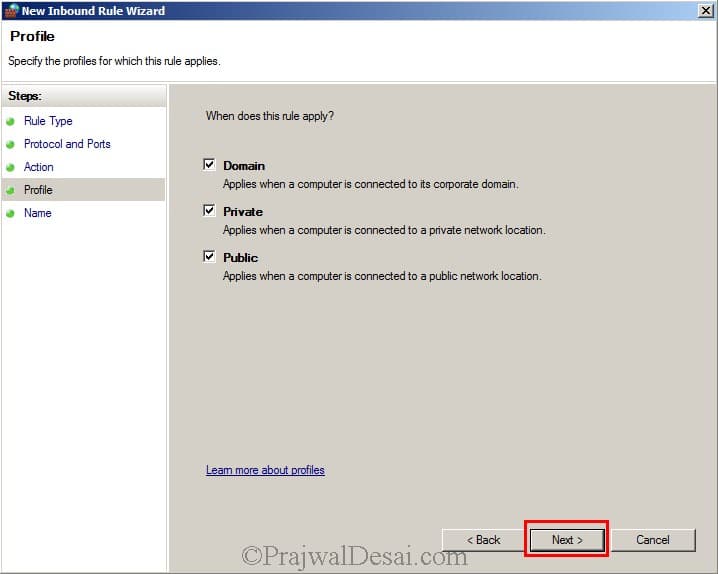
The firewall rule will be applied for all the 3 profiles. Hit Next.
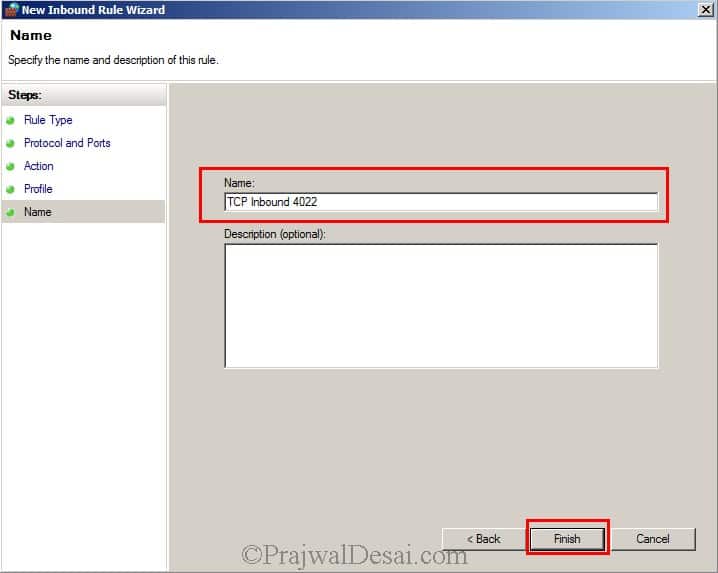
Name the rule as TCP Inbound 1433. Finally click Finish.
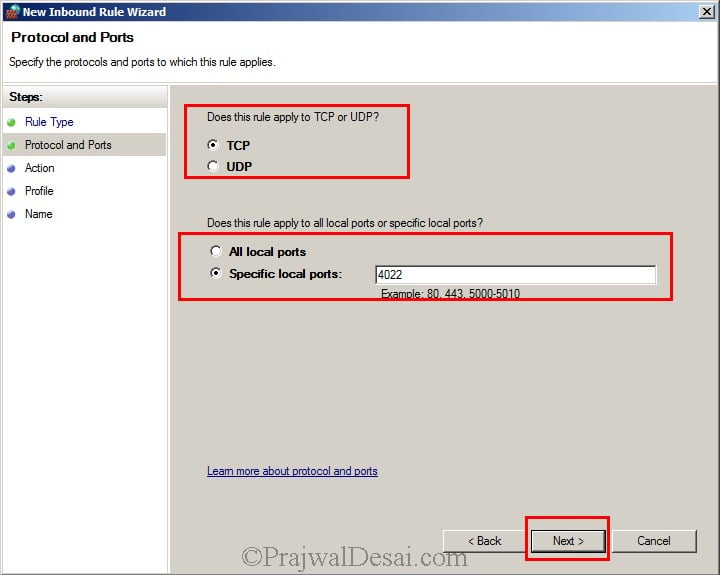
Similarly, Create an Inbound Rule for allow port 4022, choose TCP and specify the port number as 4022. Click on Next.
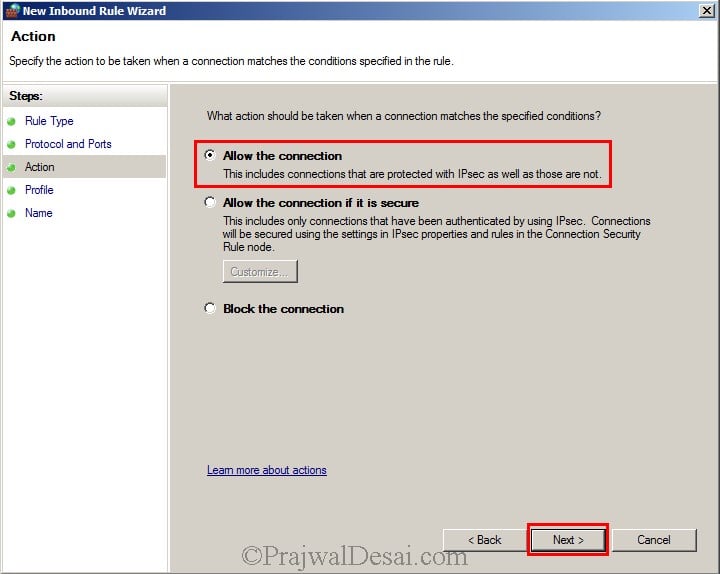
Click on Allow the connection and then click Next.
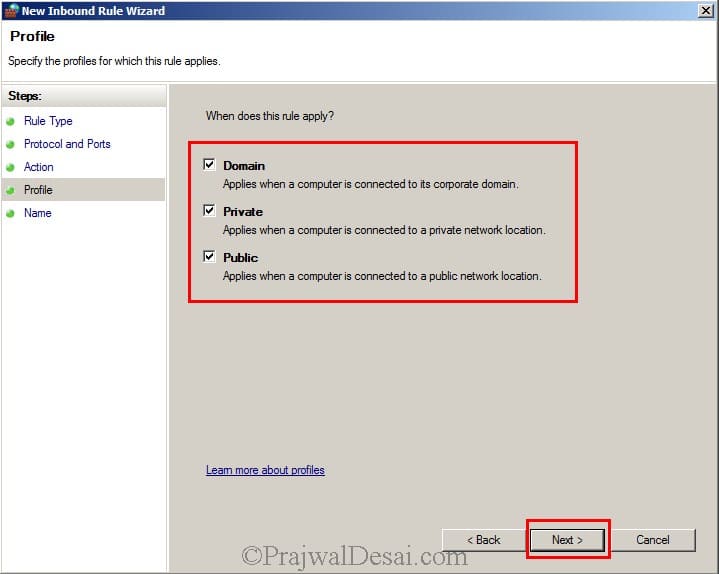
Select Domain, Private and Public and click on Next.
Provide the name as TCP Inbound 4022 to identify the rule. When you are done, hit Finish.
We have allowed TCP inbound ports 1433 and 4022 on our firewall.
On the client machine, launch the command prompt and type the command gpupdate /force and hit enter. In the same command prompt, type the command rsop.msc.
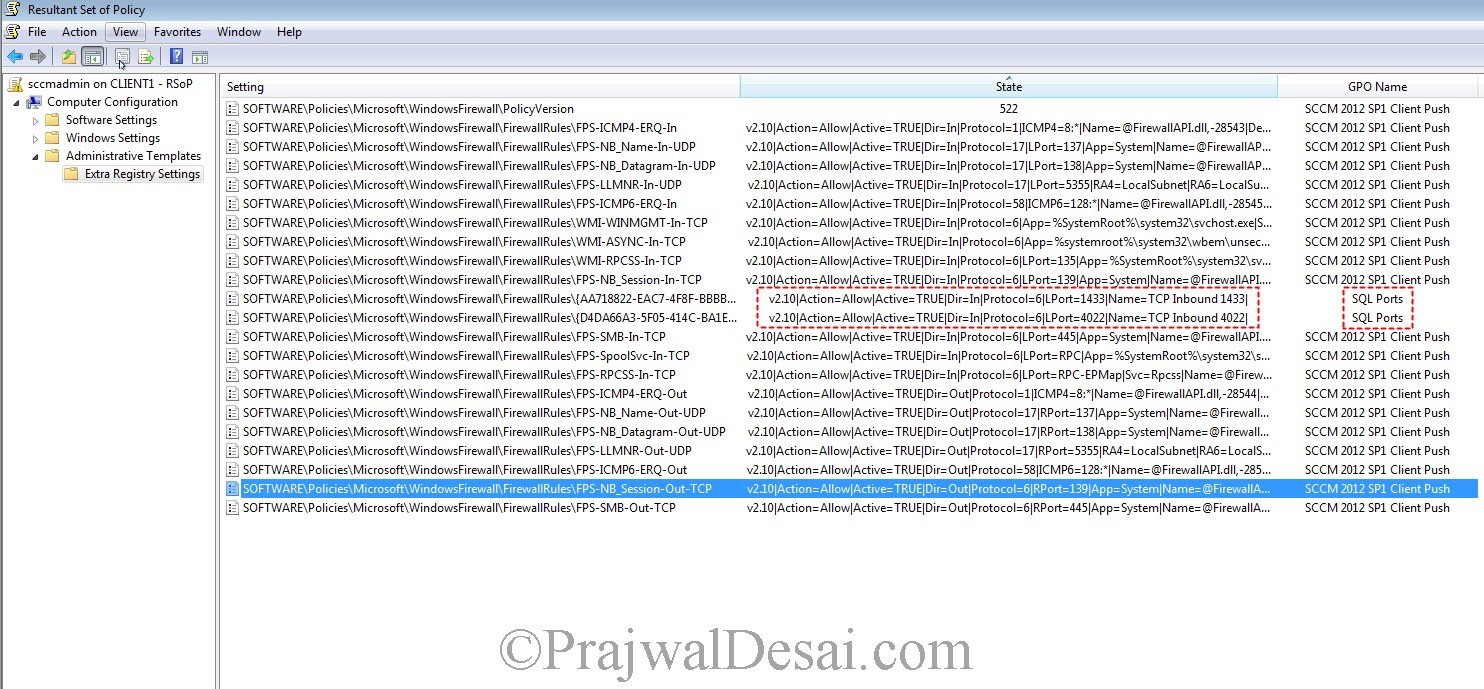
This will show the resultant set of policies, group policies that are applied to this client. Expand Administrative Templates and click on Extra Registry Settings.
On the right side pane you will find two ports 1433 and 4022 which are allowed in the firewall. This step is just to check if the policy has been pushed to the client machine or not.
























Hi there,
I read your article for installing Endpoint Protection Manager. We have an existing WSUS server that clients connect to in order to get Windows Updates.
What needs to be configured so that the clients still go directly to the WSUS server for Windows updates but get antimalware definitions from SCCM?
Is this possible?
After installing SCCM Client in all computers, can I disable/stop “File and Printer sharing service”. Is it required for CU/features update or for upgrading Operating systems.
Why do you want to disable that service ?.
Do you have a similar version for a 2016 install (with a remote instance DB)?
Or is much of the WSUS install have similar requirements?
Hi Prajawal,
Event id 1020 & Task Category: SMS_EXCHANGE_CONNECTOR
My Sytem : os windows 2008 R2, SCCM 2012 SP1 , MS Exchange 2010 sp1, wsus 3.0 with sp1 & with updated patches
Please find the Below Details.
On 01/26/14 13:57:44, component SMS_SITE_COMPONENT_MANAGER on computer xxxxxxxxxxxxxx reported: Site Component Manager failed to reinstall this component on this site system.
Solution: Review the previous status messages to determine the exact reason for the failure. Site Component Manager will automatically retry the reinstallation in minutes. To force Site Component Manager to immediately retry the reinstallation, stop and restart Site Component Manager using the Configuration Manager Service Manager.
Task Category: SMS_EXCHANGE_CONNECTOR
Event id 1020
Please give me the feedback as Mobile devices not working. Any role to be uinstall
I have install WSUS form Server Manager -> Manage -> Add Roles and Features.
So, what the next step must I do to configure WSUS?
Thanks
on the Windows 2012 Server?
If you installed WSUS, then do not configure it, the deployment of software updates is taken care by SCCM. SCCM just needs WSUS to be installed.
Hi,
I have a server that has SCCM 2012 SP1 installed, and the operating system has used is Windows Server 2012 platform.
I unable to install WSUS 3.0 SP2 on my SCCM server. When I installing the WSUS, then show the following error message :
“This program has compatibility issues”
“Windows Server Update Services Microsoft”
Why the problem? And how I can to install WSUS on Windows 2012 Server?
Thanks,
Bar Welah
The WSUS 3.0 SP2 is not compatible with server 2012. Go to Server Manager -> Manage -> Add Roles and Features and install WSUS.